

























SOC 2 is an auditing procedure that ensures service providers are securely managing personal data of customers and store customer data in a way that protects company interests and client privacy. SOC 2 compliance means providing data security and best practices to ensure that confidential information is kept private. SOC 2 certification and following the trust service criteria (TSC) are basic requirements for any contact centre software that handles sensitive information.
Bright Pattern is certified as a SOC compliant vendor. Review of Bright Pattern compliance was conducted by regulators in accordance with AT section 101, Attest Engagement (AICPA Professional Standards). Bright Pattern fulfills compliance requirements and has passed the compliance process.
Role-based and password protection.
24/7 availability with no downtime.
Define roles and responsibilities.
Encryption of all forms of interaction.
Redundant systems and a comprehensive Business Continuity and IT Disaster Recovery program to ensure no downtime.
Password complexity rules, password encryption and masking, and account lock-out ensure safety of user accounts.
Encryption of all data elements that are considered sensitive information. Regular internal scans to detect vulnerabilities.
Encryption of all interactions, including voice recordings, screen recordings, email content, chat transcripts, etc.
Limit access to authorized users based on privilege, and restrict access through unique user IDs, passwords, and access control lists.
Error-free and timely data processing to ensure fast and accurate data. Monitored through KPIs and other parameters.
By clicking the button above, I consent to Bright Pattern contacting me by phone call and/or SMS to respond to my above inquiry on services and for future marketing messages and offers. Message & data rates may apply, and message frequency may vary.

Build strong customer relationships with powerful AI-driven omnichannel contact centre software. Empower agents and boost ROI with powerful QM and AI.

Full compliance and comprehensive security features that ensure patient privacy, all while delivering seamless customer experiences.

Deliver seamless, personalized interactions to customers with AI-driven contact centre software. Featuring built-in quality management and text/sentiment analysis.
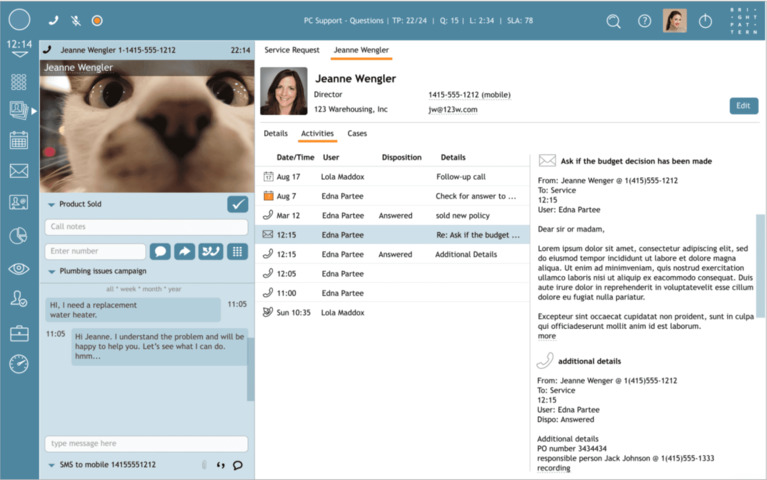
Our omnichannel contact centre solution gives your organization the ability to seamlessly communicate with clients throughout their entire customer journey.
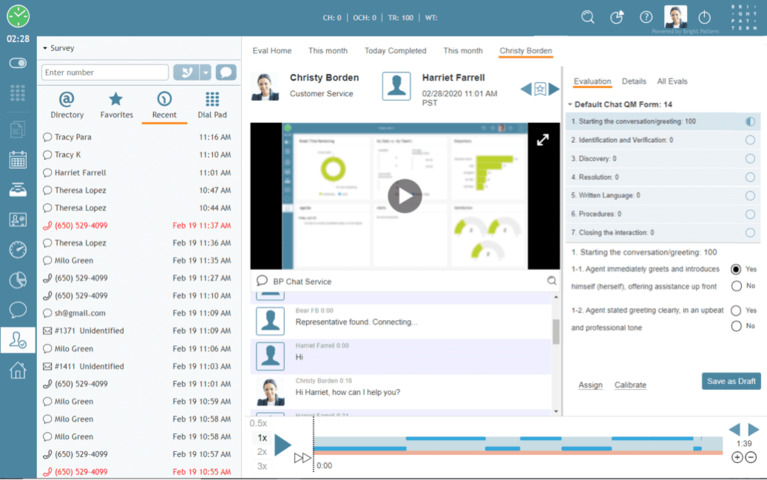
Ensure consistently excellent customer experiences and optimize call centre performance with AI-powered OmniQM.
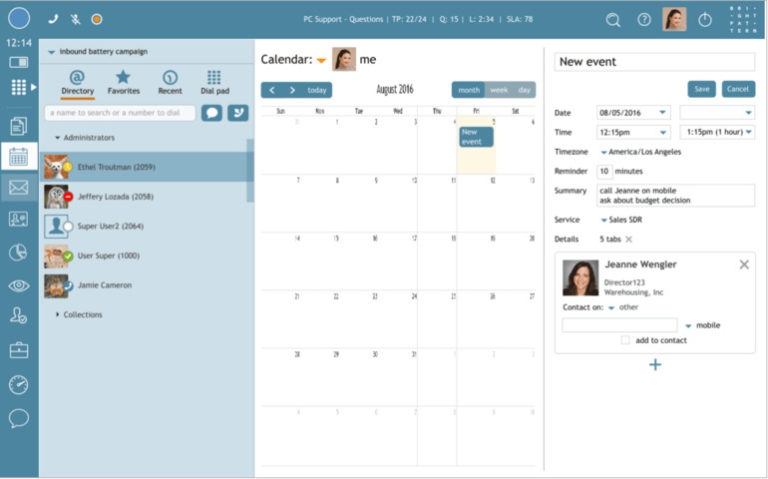
Track the customer journey with your business on any channel. Integrations with all CRM providers or your own system of records.
SOC 2, developed by the American Institute of Certified Public Accountants (AICPA or American Institute of CPAs), defines a criteria for managing customer data that are based on five “trust service principles”: security, availability, processing integrity, confidentiality, and privacy. Whether you’re a service organization, a software vendor, a government organization, or a business, it is crucial to follow these “trust principles” and pass the audit process to ensure information security and mitigation of security risk.
The SOC 2 security trust principle refers to protecting system resources against unauthorized access. Access control establishes security measures that prevent system abuse, theft of data, removal of data, tampering of data, and misuse of software. It examines physical and electronic forms of organization controls in use to ensure limited visibility to sensitive information and to mitigate the risk of security breaches and security risk.
Bright Pattern is committed to providing security to all clients and preventing unauthorized access. This is done through conducting risk assessment, testing the effectiveness of controls, and mitigating security risks. Here are the ways Bright Pattern supports security trust principles for SOC 2 Compliance:
The SOC 2 availability trust principle refers to a system being available for operation and use as specified by a contract or Service Level Agreement (SLA).
As a SaaS provider, Bright Pattern is committed to providing software with high reliability that will not experience downtime for any period of time. Here are ways Bright Pattern supports availability for SOC 2 Compliance:
The SOC 2 processing integrity trust principle refers to the system processing being complete, accurate, timely, and authorized. Processing integrity ensures that data processing is error-free and done in a timely fashion within a service organization’s system. It provides peace of mind and assurance that the data is accurate. For businesses that offer financial or e-commerce transactions, audit trails, financial reports, and auditors should include details on controls designed to safeguard transactions.
Bright Pattern, as a provider of software that processes sensitive information and customers’ data, follows processing integrity through the following ways:
The SOC 2 confidentiality trust principle refers to data that is restricted to a specified set of persons or organizations and is protected according to policy agreement. Confidentiality ensures specific sets of client data are restricted to a specified set of persons within the entire organization and sensitive data is kept safe.
Bright Pattern, utilizing cloud services and handling client data, ensure confidentiality through the following ways:
The SOC 2 privacy principle refers to personal information that is collected, used, retained, disclosed, and destroyed in conformity with the commitments in the entity’s privacy notice and with criteria set forth in generally accepted privacy principles (GAPP). The privacy principle differs from the confidentiality principle through it’s safeguarding of personal information. Personal information can include name, social security number, address, and financial information.
Bright Pattern’s software provides privacy through the following:
Bright Pattern, being a top provider of cloud contact centre software, is committed to protecting sensitive information through the implementation of encryption, access controls, and 24/7 availability. Our contact centre software implements features that make Bright Pattern SOC compliance in accordance with the purpose of SOC standards. Aside from SOC compliance, Bright Pattern is also PCI, GDPR, TCPA, and HIPAA compliant.
By clicking the button above, I consent to Bright Pattern contacting me by phone call and/or SMS to respond to my above inquiry on services and for future marketing messages and offers. Message & data rates may apply, and message frequency may vary.
By clicking the button above, I consent to Bright Pattern contacting me by phone call and/or SMS to respond to my above inquiry on services and for future marketing messages and offers. Message & data rates may apply, and message frequency may vary.
By clicking the button above, I consent to Bright Pattern contacting me by phone call and/or SMS to respond to my above inquiry on services and for future marketing messages and offers. Message & data rates may apply, and message frequency may vary.